The key to secure your reputation

In order to provide our customers the best possible overview of the cyber security state in the company, we are simulating a staged cyber-attack in order to find the vulnerabilities in your companies IT system.
With our penetration test report we provide your organization with a detailed and comprehensive analysis of the vulnerabilities areas which needs to be addressed. Furthermore we provide you with possible solutions scenarios to avoid cyber-attacks from being successful in your company or organization.
External and internal penetration test
The penetration test is divided into an external and internal testing scope which gives the best guarantee that all the security breaches in your system will be found and handled in the right manner.
An external penetration test emulates the most typical cyber-attack which aims at gaining access to your critical infrastructure from public areas of your company which are accessible from the public internet.
The internal penetration test focuses on your IT environment behind the firewall and simulates a cyber-attack when the attack outmanoeuvred your defence mechanism and has already access to your companies digital assets.
Penetration test stages
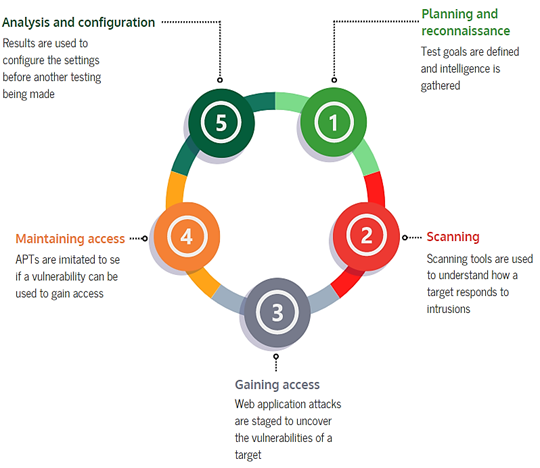
The penetration test is performed in five stages:
- Scoping and intelligence gathering
- How will the target respond to a cyber-attack?
- Which vulnerabilities does your system have?
- Can the vulnerabilities be used to gain access to your system?
- Analysis of the Penetration test result and reporting
After the completion of the stages we are able to provide you detailed information on vulnerabilities that were exploited and the accessed data. Furthermore we are able to tell you the time amount in which our experts had access to your critical infrastructure and remained undetected in your system.
