Desoma’s Demon is a Next Generation
Cyber Defence Software
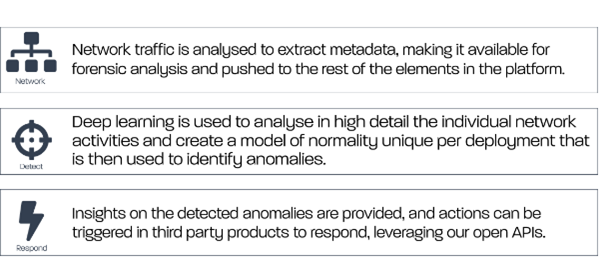
Demon is based on a government proven, real time data extraction and analytics engine. Demon offers customers and partners an intuitive, easy to use interface to view and analyze all IP-data transmitted.
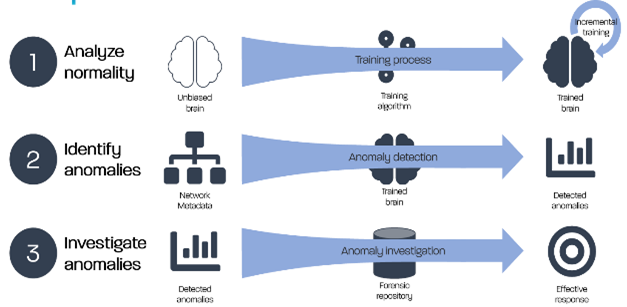
The clear aim of Desoma’s Demon is to reduce the manpower and time needed for an analysis of vast amount of big data. With the use of our own fully embedded Deep Learning algorithms we are able to generate actionable cyber threat anomaly alarms.
A very welcoming side effect is the significant reduction of the false positive rate of alarms allowing the Analyst to act in a timely fashion as the attack happens!
An Unbiased Network Detect & Response
Features
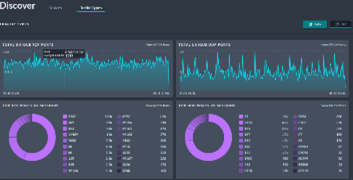
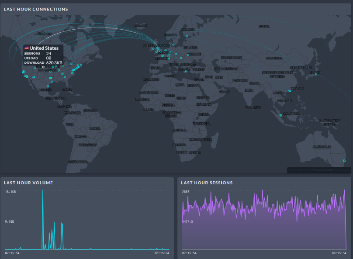
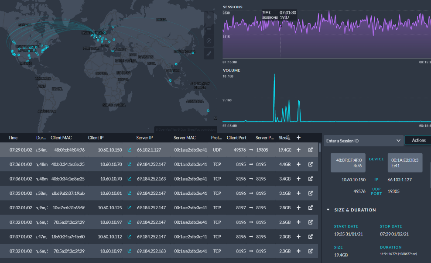
Demon passively plugs into organisations’ networks to provide in-depth visibility of the activities across the whole organisation, with Metadata extraction up to Layer 7.
Demon is architected to be highly available and scalable via an optimised technology stack. It provides analysis of weeks of data (4 weeks retention by default) allowing ultrafast drill-down to specific relevant network sessions.
The Demon frontend is a highly visual interface to assist in manual or automated threat hunting, device discovery, traffic trends and highly specific filtering. Cases may be created once anomalies are identified to provide collaborative investigations.
Demon provides a complete feature set to support the end-to-end processes of security teams, including a secured Application Program Interface (API) to integrate with your existing infrastructure to leverage existing investments. Demon includes a self-documented GraphQL API providing data access and generation of actions in the platform. Webhook triggers may be created from platform events and alerts to third party systems, triggering actions in systems such as SIEM, SOAR, Ticketing systems or Firewalls/NAC/EDR etc.
Train – Detect — Investigate
Specification
- Zero-Loss real-time analytics
- Port and protocol independent
- Meta-Data Layer 2–7
- Special focus on Zero-Day attacks and Trojans [single sided session]
- State of the art Deep Learning algorithms
- Use of commercial-of-the-shelf hardware (COTS)
- No active interference with the transmitted data
- Government proven & GDPR compliant
- Full on prem installations – no customer data is transferred